Services
Certificate
Electronic transactions, which cover transactions in both the business sector and government services in e-government, including transactions for citizens or consumers, are becoming increasingly important, especially in creating added economic value and improving the quality of life of citizens. However, communicating online to conduct transactions also involves the issue of trust that a person, website, service provider (server), or any device, or any information system, or any entity is a person or thing. This is the origin of the development of Public Key Infrastructure (PKI) technology.
OCSP Service
Online Certificate Status Protocol: http://ocsp.nrca.go.th
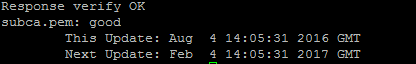
$openssl ocsp -nonce -CAfile rootca.pem -issuer rootca.pem -cert subca.pem -url http://ocsp.nrca.go.th
Subordinate CA
List of Certification Authorities (CAs) under the Thailand National Root Certification Authority (Thailand NRCA)
The Electronic Transactions Development Agency (ETDA) as the operator of the Thailand National Root Certification Authority (Thailand NRCA),
has conducted the qualification assessment of electronic certificate issuers (Certification Authorities – CAs) based on the WebTrust for Certification Authorities criteria established by CPA Canada, which is a widely recognized international standard for CA operations.
Entities wishing to become Certification Authorities under the Thailand NRCA are required to undergo an independent audit conducted by a WebTrust Practitioner and obtain the WebTrust Seal—a mark of trust that affirms compliance with global best practices and security standards. ETDA is pleased to announce the list of Certification Authorities (CAs) that have been officially recognized and operate under the trust framework of the Thailand NRCA, as follows:
Training Course
Thailand NRCA now offers comprehensive training courses on Public Key Infrastructure (PKI) and related standards, empowering individuals and organizations to enhance their cybersecurity capabilities. The program is designed to prepare participants to become internationally recognized Certification Authorities (CAs), enabling them to provide electronic certificate services at a global level. Our courses cover both theoretical and practical aspects, delivered by experienced industry experts.
News/Article



FAQs

Public key infrastructure (PKI) is technology that uses public key cryptography consisting of the private and public keys. The aforementioned structure is used in authentication including data confidentiality, data integrity and non-repudiation. Public key infrastructure consists of the Certification Authority (CA), the Registration Authority (RA), the Directory Service and the Subscriber.

Electronic certificates can be used with the following two characteristics:
- Digital signatures certify electronic data as data sent by the referred sender. Digital signatures are used to test data for forgeries during the sending step such as signatures countersigning electronic mail. The sender will use the sender’s private key to countersign that electronic mail, thereby ensuring that the electronic mail was sent by the referred sender. In examinations, the recipient will need to use the public key on the sender’s certificate to examine the sent electronic mail to determine the data in the electronic mail was sent from the sender without being forged during the sending step.
- Encryption converts normal data to a type of data that cannot be read and understood to prevent others from knowing about the data such as electronic mail encryption. The sender will use the recipient’s public key (on the recipient’s certificate) to encrypt. In decryption, the recipient will have to use the recipient’s private key to decrypt. Using the private key to decrypt ensures that only the recipient who owns the key pair (private and public keys).

Electronic certificates are electronic data issued by the Certification Authority for authentication in the electronic world. The Certification Authority will certify data including the public key appearing on electronic certificates to determine electronic certificates belong to that person suing public key infrastructure technology (PKI).

- Data confidentiality prevents other persons who are not permitted or do not have rights from reading electronic data.
- Data integrity enables testing the received data for integrity and in determining the data was not edited.
- Authentication confirms the identity of the person who sent electronic data.
- Non-repudiation prevents the sender from denying that the sender did not send electronic data

In using electronic certificates issued by CAs, users may sometimes encounter interoperability problems from certificates issued by different CAs. Therefore, the Trust Model between CAs was developed by certifying the electronic certificate issued by each CA in a hierarchy with one CA functioning to certify electronic certificates from other CAs in addition to being at the highest level popularly known as the “Root CA”. The Electronic Transactions Committee oversees policy planning regarding the country’s electronic transactions and approved the use of the Trust Model in the form of Root CA in Thailand.

The Thailand National Root Certification Authority will function as a center for building confidence in using the PKI system to create interoperability between domestic CAs in addition to being the center for contacting foreign CAs. This will enable service users under different CAs to communicate without obstacles in addition to building confidence in online transactions. This will increase the country’s overall economic value in the future.







